Highlight
Secrets should remain secret, but they are not by default.
Intro
If you ever developed any integration using Azure logic apps, you probably appreciate how easy is it to debug your workflows using visual designer. Everything is clear and well laid out, every action can be reviewed with all input and output parameters. It’s trully a fantastic way to build solutions.
Problem Statement
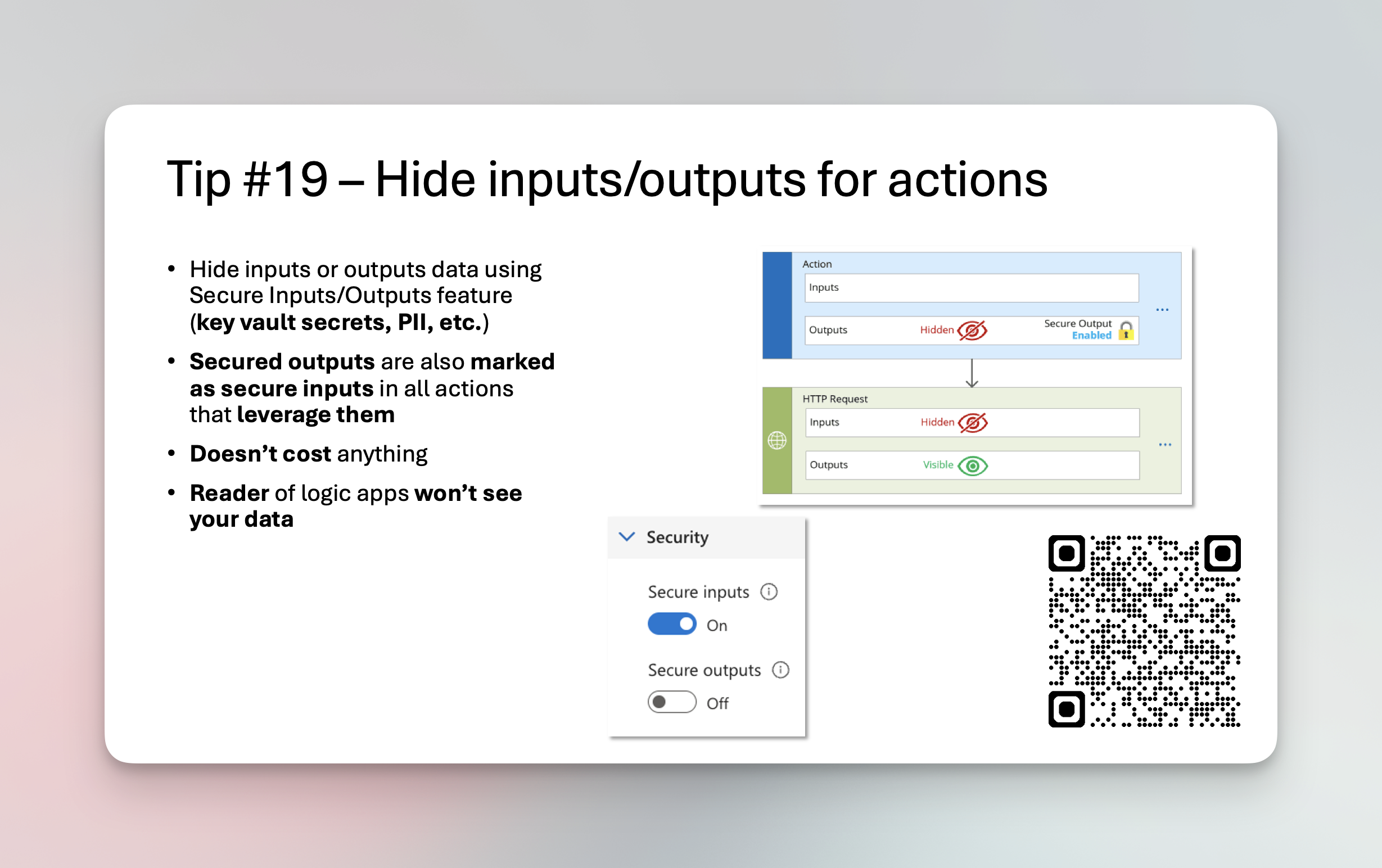
But, have you ever built a workflow which requires you to connect to key vault to grab a secret key, or some external API to generate some sort of API key, or maybe you needed to add a secret parameter. If you ever did that, then you know all these secrets will be visible in those logs that we all priase so much.
So what now?
Solution
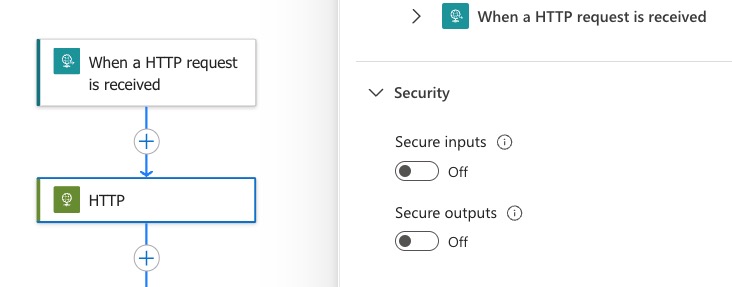
There is a feature called Secure Inputs and Secure Outputs which is available on almost any action in Logic Apps. It’s pretty neat. The way it works is that it hides the values from the logic app run history.
How it works?
If you want to hide for example a secret value you retreived from the key vault, you just mark the action with Secure Outputs and it will take for you all of that.
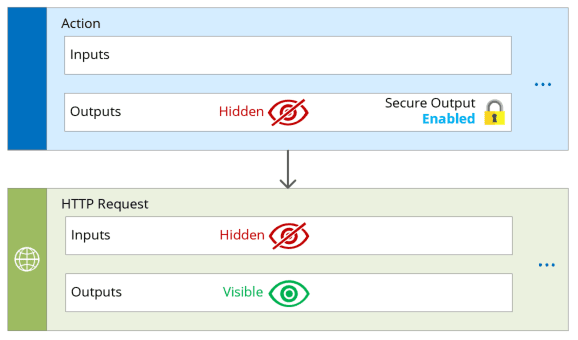
The coolest thing is that every action which takes as an input, a value from a previously secured output. It will automatically get marked as secure input. Hence the value will not be shown in all dependant actions. Although, you use it in expression, it’s stil possible you will see it.
Need extra info? Read more.
If you want to learn more about how it work, feel free to read it here.
- Blog post Logic Apps Secret Obfuscation
Summary
Secrets should never be exposed, under any circumstances. Whether that’s CICD logs, log analytics diagnostic or app logs, or just azure portal UI & logs. Secrets should always remain as the name suggests, a secret. This feature will allow you to achieve that.

