Navigation
- Skills Learned
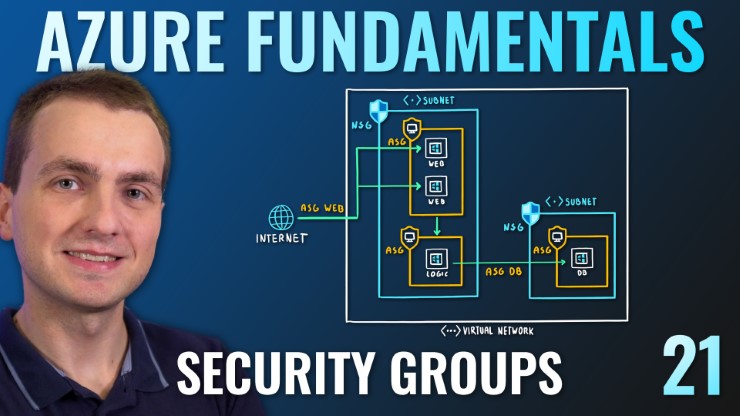
- Describe Network Security Groups (NSG)
- Describe Application Security Groups (ASG)
- Study Guide
Practice Test
◀ Previous Episode
Next Episode ▶
Adam Marczak
Programmer, architect, trainer, blogger, evangelist are just a few of my titles. What I really am, is a passionate technology enthusiast. I take great pleasure in learning new technologies and finding ways in which this can aid people every day. My latest passion is running an Azure 4 Everyone YouTube channel, where I show that Azure really is for everyone!
Did you enjoy the article?
More tagged posts