Highlight
Do you need to protect your logic app with HTTP Entra ID authentication? Don’t get fooled by online blogs on this. You don’t need APIM!
Intro
Entra ID authentication with OAuth is a staple of how you authenticate requests in Azure to any API. It’s just a perfect solution as it takes away all the complexity of rotating keys and managing security at scale.
If you develop logic app which act as web services, i.e. they have HTTP Request Trigger, then by default this logic app is protected with a SAS token authroization.
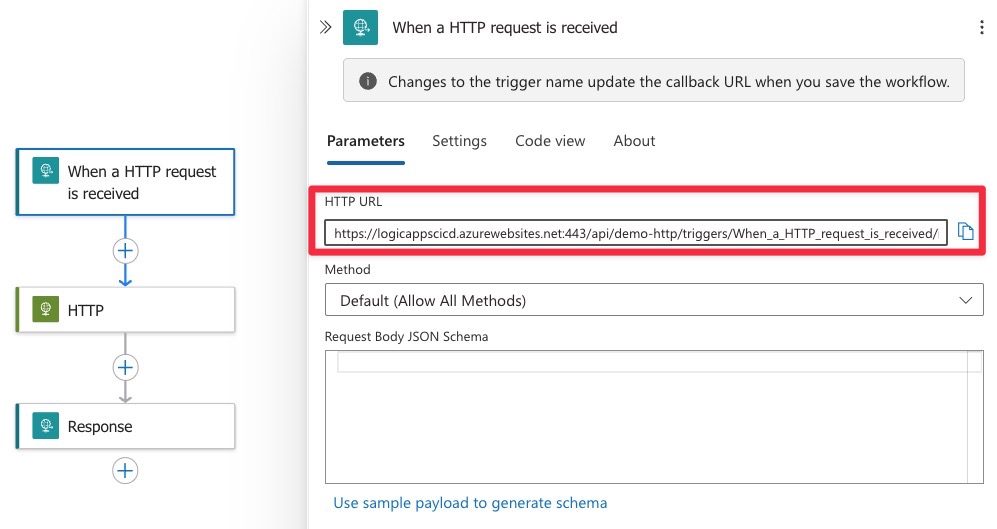
A full URL with SAS token looks like this
https://logicappscicd.azurewebsites.net:443/api/demo-http/triggers/When_a_HTTP_request_is_received/invoke?api-version=2022-05-01&sp=%2Ftriggers%2FWhen_a_HTTP_request_is_received%2Frun&sv=1.0&sig=qVukkGoYcS3mx5r_R2Vt423enLnFOP1Qkg-kq__L_U3xE
Where the SAS is exactly the part after sig=.
sig=qVukkGoYcS3mx5r_R2Vt423enLnFOP1Qkg-kq__L_U3xE
Ref: Generate a shared access signature (SAS) key or token
Problem Statement
The biggest issue of using SAS token is that if user leaves project / or even company, it continues to work, exposing your project to a risk. But there are many scenarios where this can screw up your project/platform
- Your developer mistakenly commits key to a public repository
- Your key gets stolen by a bad actor
- Developer makes a mistake and uses key in prod instead of switching to dev
- etc…
It’s just a risk of using it. But there is a better way, which is turning off SAS token authentication and using Entra ID authentication instead.
Solution (Consumption Logic Apps)
If you search the web on how to enable Entra ID authentication
Step 1 - enable Entra ID auth
Authorization Policies is a way to allow users and solutions to authenticate to your logic app HTTP endpoints using Entra ID (service principals / managed identities). It’s just a few clicks on done.
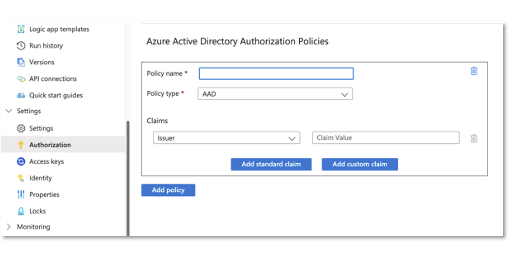
Here is MS’s guide on how to do it step by step
Ref: Enable OAuth with Microsoft Entra ID for your Consumption logic app resource
Step 2 - disable SAS auth
In logic apps consumption the authentication pattern requirement uses “OR” logical statement
So if you enable EntraID auth, you will end up with two authentication/authorization schemed available
- SAS token
- Entra ID using Bearer token
If you pass key, you will skip entra ID auth, so it’s recommended to disable it.
So you need to disable SAS token, and the way you do it is by making a small addition into your logic app
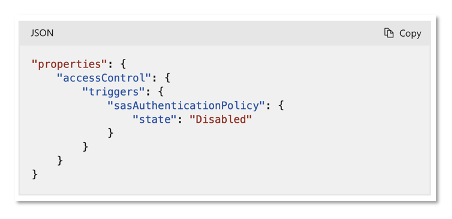
Copy-paste :)
"properties": {
"accessControl": {
"triggers": {
"sasAuthenticationPolicy": {
"state": "Disabled"
}
}
}
}
Ref: Disable shared access signature (SAS) authentication (Consumption only)
Solution (Standard Logic Apps)
For Standard Logic Apps, because they are hosted on Azure App Services, you can leverage EasyAuth. it’s a built in feature of Azure App Service that allows you to protect all hosted APIs with Entra ID, and it works with logic apps too!
Here is MS’s guide on how to do it
Summary
As you see, there are ways to protect your Azure Logic App endpoints with Entra ID authentication without a need for APIM. While APIM is great and can serve that purpose as well, it’s not as cheap. These features are free and you can leverage them Today without any extra knowledge.
APIM still should be used, don’t get me wrong. Just you don’t have to for this particular reason.

